

The Fortinet Security Fabric provides broad, integrated, and automated protection across the organization—on-premises, across multiple clouds, and out to users and devices. For those using Microsoft 365, key Security Fabric elements include email security with FortiMail, FortiCASB to monitor Microsoft 365 usage, data, and configurations, as well as tools for multi-factor authentication, zero-trust network access, and endpoint security. The Fortinet Secure SD-WAN solution delivers a fast and secure connection to Microsoft 365 and other cloud-based applications while adhering to Microsoft 365 networking principles and guidelines.
Add Extra Protection for Exchange Online
Email is the delivery vehicle for 92.4% of all malware, and 49% of successfully installed malware.1 Beyond malware, email can lead users to phishing sites, expose them to scams, and can be used to extract sensitive information from your network. Microsoft offers security packages for M365 such as Exchange Online Protection and Advanced Threat Protection. But even when fully implemented and properly configured, Microsoft’s security solutions accurately detect less than 30% of malicious emails. To protect your users, customers, and your business, it is critical to deploy email security tools. FortiMail and FortiCASB enhance Microsoft 365’s native security with:
Lead with FortiMail for Integrated Protection
Providing comprehensive protection for cloud solutions is a challenge, with Software-as-a-Service (SaaS) vendors like Microsoft controlling not just the infrastructure but also the application layer. Fortunately, it is now common practice for major cloud providers to provide APIbased access to their offerings to applications for just that purpose. This allows Fortinet FortiCASB to complement the in-built visibility of the Microsoft 365 Admin Center, security tools to assess and report on users, behaviors, and data associated with Microsoft 365 and other SaaS applications. More importantly, it also enables advanced FortiCASB functions to extend security policies and intelligence and data centers.
Specifically, Microsoft 365 customers are able to:
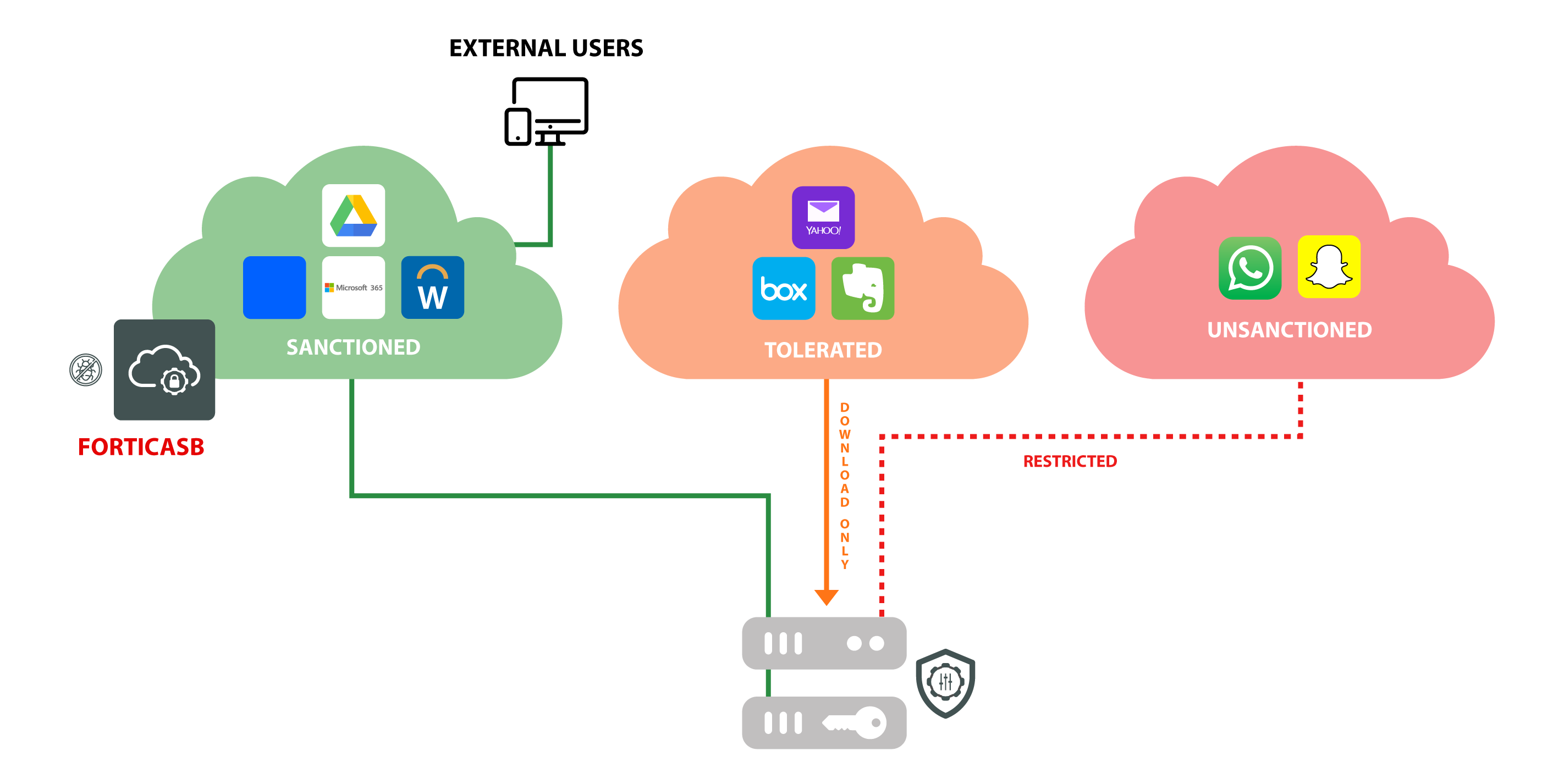
FortiCASB integrates with Microsoft 365 and extends security and SaaS clouds.
Ensure Strong Identity and Access Management
Of course, it does not take malware for cyber criminals to enter Microsoft 365, nor employee error for sensitive data to leave it. As of 2020, top cyber criminal techniques resulting in breaches still include the use of stolen credentials. That’s why Fortinet offers FortiToken (and optionally FortiAuthenticator) Identity and Access Management (IAM) products. Commonly used in conjunction with the Active Directory (AD) services of Microsoft 365 that enable single sign-on, federation, vand more, Fortinet IAM solutions take security to the next level:
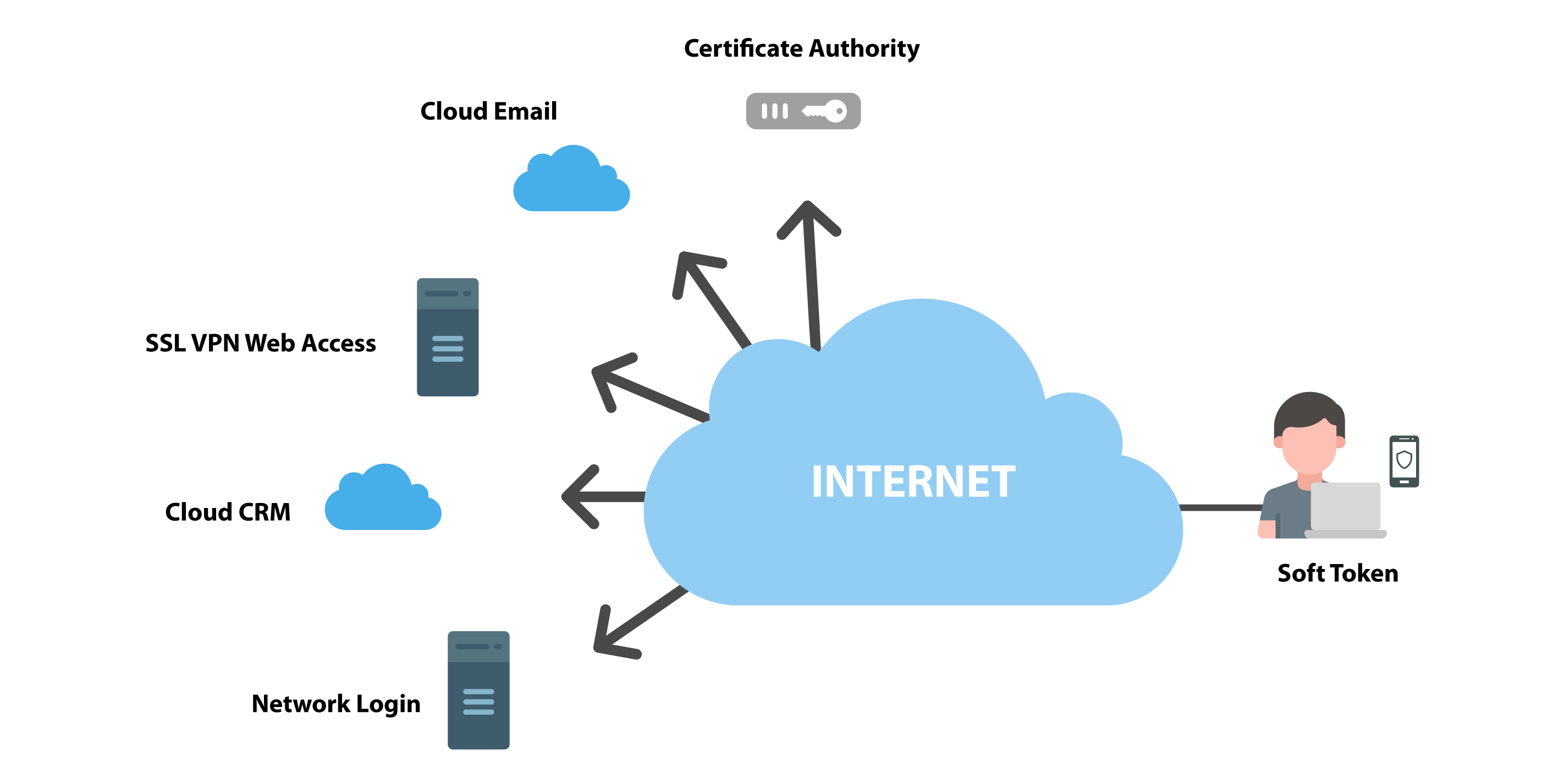
FortiToken helps protective sensitive data on and off network across clouds of all types.
Why Fortinet
There are plenty of third-party vendors to choose from, especially across multiple components like CASB, Email Security, and Identity and Access Management. There are three primary things that set Fortinet apart from the rest:

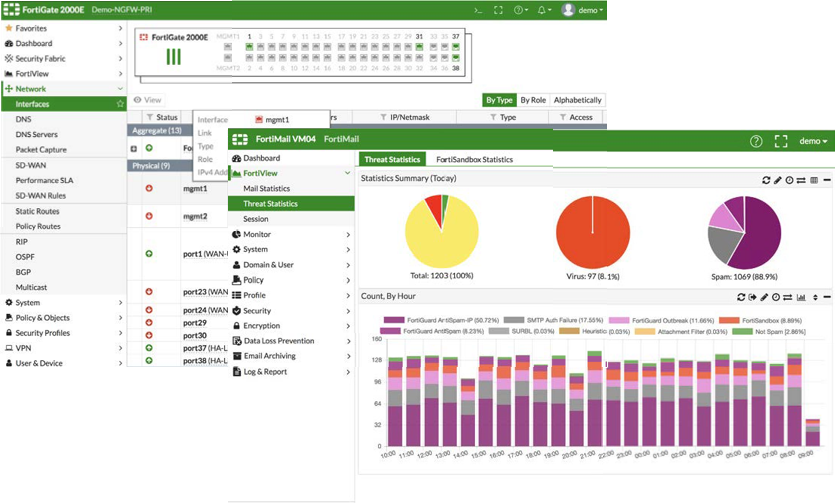
Fortinet offers a common user interface across security components for microsoft 365.

3F Citibank Center
8741 Paseo de Roxas
Makati City, Philippines
CFI@commerce-first.com
Trunk Line: +632 8893 6657
Fax: +632 8815 8650
© COPYRIGHT 2021 COMMERCE FIRST. INC. (CFi)
All third party trademarks (including logos and icons) reference by Commerce First Inc., (“CFi”) remain the property of their respective owners. Unless specifically identified as such, CFi’s use of third party trademarks does not indicate any relationship between CFi and the owners of these trademarks. Any references by CFi to third party trademarks is to identify the corresponding third party goods and/or services and shall be considered nominative fair use under the trademark law.